In the world of digital marketing, MMO, and online business, the terms VPN and Proxy are often used interchangeably. This common confusion is understandable; after all, both services can hide your IP address, making you appear as if you’re browsing from a different location. However, this is where the similarities end. A VPN and a proxy operate in fundamentally different ways, and understanding this difference is critical to protecting your data, your accounts, and your online operations. This article will dissect the VPN vs. proxy debate, focusing on the one factor that truly matters: encryption.
What is a Proxy Server? A Basic Overview
A proxy server acts as an intermediary between your device and the internet. When you send a request (for example, to visit a website), it first goes to the proxy server. The proxy server then forwards that request to the website using its own IP address. The website sends the data back to the proxy, which in turn relays it back to you. For the website, it looks like the proxy server is the one visiting, not you. This is how a proxy masks your real IP address.

There are several types of proxies, but the most common are:
- HTTP Proxies: These are the simplest type and are designed exclusively for web traffic (HTTP and HTTPS). They are often used for accessing geo-restricted content but typically offer no security.
- SOCKS5 Proxies: These are more versatile than HTTP proxies because they work at a lower level and can handle any type of traffic, including for applications like streaming, gaming, or torrenting. While more flexible, they don’t inherently add encryption.
The primary issue with most proxy services, especially free ones, is their complete lack of encryption. Your data travels in plain text between your device and the proxy server, making it vulnerable.
What is a VPN? The Digital Bodyguard
A Virtual Private Network (VPN) creates a secure, encrypted “tunnel” between your device and a server operated by the VPN provider. All your internet traffic—not just from your browser, but from every application on your device—is routed through this tunnel.
Because the connection is encrypted, no one can see the data passing through it. Not your Internet Service Provider (ISP), not network administrators, and not malicious actors on a public Wi-Fi network. Like a proxy, the VPN server replaces your IP address with its own, effectively masking your location and identity. The key difference is that a VPN protects your data’s entire journey.
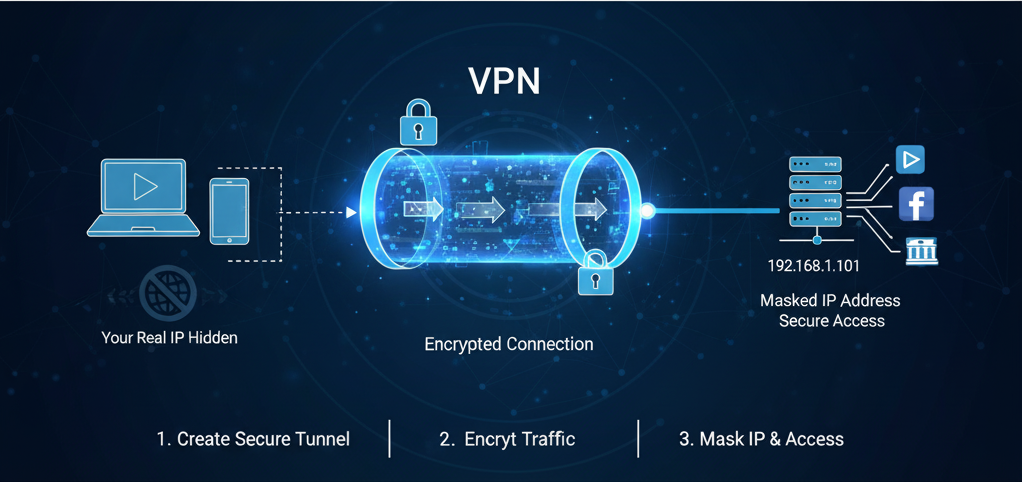
Encryption: The Decisive Factor in the VPN vs. Proxy Debate
This is the heart of the matter. The presence of robust encryption is what elevates a VPN far beyond a simple proxy for security and privacy. While a proxy simply reroutes your traffic, a VPN fundamentally secures it.
Think of it like sending a postcard versus a sealed, armored letter. A proxy is the postcard: the postman (the proxy server) changes the return address, but anyone along the delivery route can read the message. A VPN is the armored letter: not only is the return address changed, but the message itself is locked in a secure box that only you and the intended recipient have the key to open. This “key” is encryption.
The lack of encryption in most proxies exposes you to significant risks, especially for business and MMO activities:
- Data Interception: On public Wi-Fi or compromised networks, hackers can easily intercept unencrypted traffic from a proxy to steal login credentials, financial information, and sensitive business data.
- ISP Monitoring: Your ISP can still see every website you visit when you use a proxy. With a VPN, your ISP only sees that you are connected to a VPN server; the encrypted data passing through is unreadable.
- Malicious Proxies: Free proxy servers are notorious for being untrustworthy. Some are deliberately set up to monitor your traffic and inject ads or even malware into your browsing sessions.
Scope of Protection: Application-Level vs. OS-Level
Another crucial difference is the scope of their operation. A proxy is typically configured on an application-by-application basis. You might set up a proxy in your web browser, but your other applications—like your email client, social media management tools, or gaming platforms—will still connect directly to the internet using your real IP address. This leaves significant security gaps.
A VPN, on the other hand, operates at the operating system (OS) level. Once you connect to the VPN, it captures and encrypts all internet traffic leaving your device, regardless of which application it comes from. This provides comprehensive, system-wide protection, ensuring no data leaks or accidental IP exposure.
VPN vs. Proxy: A Head-to-Head Comparison
To summarize the key differences, here is a clear, side-by-side comparison table:
| Feature | VPN (Virtual Private Network) | Proxy Server |
|---|---|---|
| Encryption | Strong, end-to-end encryption. All traffic is secured. | Usually none. Traffic is sent in plain text (unless it’s an SSL proxy). |
| Scope of Protection | Operating System Level. Protects all applications on your device. | Application Level. Typically configured for a single app, like a browser. |
| Security | High. Protects against ISP monitoring, hackers, and government surveillance. | Low. Offers no protection against data interception. Free proxies can be malicious. |
| Privacy | High. Hides your IP and encrypts your activity. Reputable VPNs have no-logs policies. | Low. Hides your IP but your activity can be monitored by the proxy owner and your ISP. |
| Speed | Can slightly reduce speed due to encryption overhead, but premium services are highly optimized. | Can be very slow, especially free public proxies that are often overloaded. |
| Cost | Typically a paid subscription service. | Many free options are available, but premium/private proxies are paid. |
| Primary Use Case | Comprehensive online security, privacy, accessing censored content, safe public Wi-Fi use. | Bypassing basic geo-restrictions, web scraping, managing multiple low-stakes accounts. |
Conclusion: Make the Right Choice for Your Digital Operations
The VPN vs. proxy debate has a clear winner when security and privacy are your priorities. While a proxy can offer a quick way to change your IP for simple tasks, its lack of encryption makes it an inadequate tool for any serious online work. It leaves your data exposed and your accounts vulnerable.
A VPN is the superior solution for comprehensive protection. Its system-wide encryption secures all your online activities, making it an essential tool for digital marketers, MMO players, and businesses that need to manage multiple accounts and handle sensitive information securely.
Ready to Secure and Automate Your Operations?
For professionals managing complex digital tasks, a standard VPN is just the beginning. At GenFarmer, we understand that you need robust, reliable, and scalable solutions. Our ecosystem is designed to provide ultimate control and security for your projects.
- GenFarmer Router Proxy: Go beyond a simple VPN. Our specialized hardware allows you to manage multiple, stable IP addresses with ease, providing the dedicated and clean connections essential for successful phone farm and automation tasks.
- Box Phone Farm Hardware: Build a powerful and secure automation setup with our industry-leading hardware, designed for performance and stability.
- Cloud Phone Solutions: Need flexibility? Our cloud phones offer a secure, virtualized environment to scale your operations without the hardware overhead.
Don’t compromise on security. Explore the GenFarmer ecosystem today and equip your business with the professional tools it needs to thrive securely.











