You invest in a Virtual Private Network (VPN) for a promise: online privacy and security. It’s your digital invisibility cloak, meant to shield your real identity from websites, your Internet Service Provider (ISP), and prying eyes. But what if that cloak has a hole? A VPN is only as good as its ability to contain your real data. Even a small leak can expose your IP address, revealing your location and online activities, completely defeating the purpose of using a VPN in the first place. This guide provides a straightforward, technical, yet accessible walkthrough for any VPN user to verify their service is working correctly and not leaking their personal information.
1. What Is an IP Leak?
An IP leak is a security flaw that occurs when, despite being connected to a VPN, your device’s true IP address is revealed to websites or third parties. Your IP address is a unique identifier assigned to your network, much like a physical street address. It can be used to pinpoint your geographic location and track your online behavior. A VPN is supposed to mask this by routing your traffic through one of its own servers, making it appear as if you are browsing from the server’s location. When this process fails, an IP leak occurs, and your anonymity is compromised.
This vulnerability means your ISP, advertisers, and even malicious actors can see your real location and browsing habits. For those in digital marketing or managing multiple online accounts, an IP leak can lead to account suspension, failed campaigns, and a loss of trust. Ensuring your VPN is working correctly is not just a suggestion; it’s a critical security check.
2. How to Check for an IP Address Leak (Basic Verification)
The most fundamental test is to check if your public-facing IP address changes when you connect to the VPN. This simple verification is your first line of defense in determining if your VPN is performing its most basic function. Follow these steps carefully.
2.1. Step 1: Find Your Real IP Address
First, make sure your VPN is disconnected. Open your web browser and navigate to an IP verification website. There are many reliable options, such as Whoer.net or whatismyipaddress.com. The site will display your public IP address, your ISP, and your approximate location. Write this IP address down.
2.2. Step 2: Connect to Your VPN
Now, launch your VPN application and connect to any server. It could be in a different city or a different country. Once the connection is established, your VPN should be actively routing all your internet traffic through that server.
2.3. Step 3: Re-Check Your IP Address
Return to the same IP verification website you used in Step 1 and refresh the page. The IP address, ISP, and location displayed should now be completely different. They should correspond to the location of the VPN server you selected. If the website still shows your real IP address from Step 1, you have a critical IP leak. This means your VPN is not masking your identity at all, and you should stop using it immediately until the issue is resolved.
3. How to Check for a DNS Leak
An IP leak isn’t the only threat. A DNS leak can be just as revealing. The Domain Name System (DNS) acts as the internet’s phonebook, translating human-readable domain names (like genfarmer.com) into machine-readable IP addresses. By default, these requests are handled by your ISP’s DNS servers.
A secure VPN should handle these requests through its own encrypted tunnel, using its own private DNS servers. A DNS leak occurs when these requests bypass the VPN tunnel and go directly to your ISP. Even if your IP is hidden, a DNS leak allows your ISP to see every single website you visit. This is a significant privacy breach.
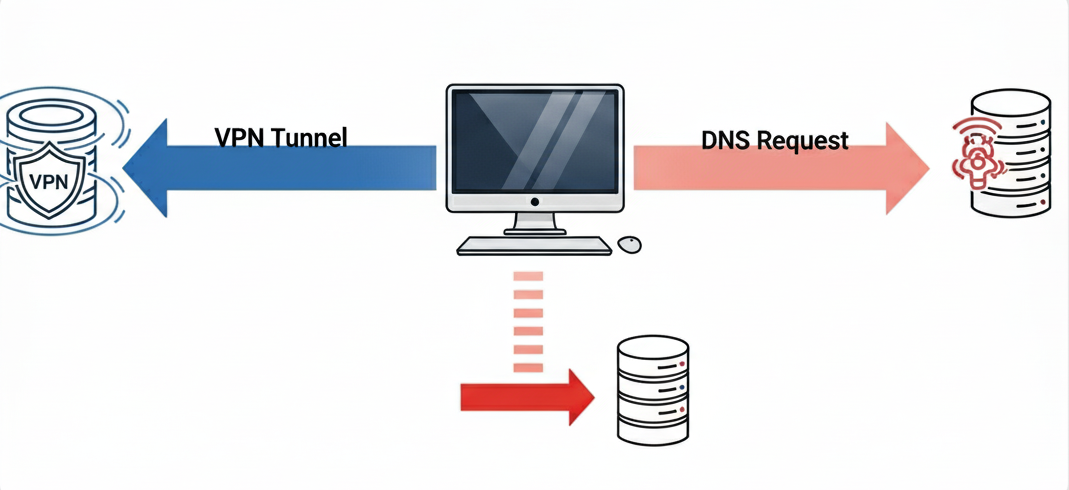
3.1. How to Verify a DNS Leak
To check if your VPN is working without DNS leaks, use a specialized online tool. With your VPN connected, go to a site like DNSLeakTest.com.
- Run the “Standard Test.” The website will send a series of queries to see which DNS servers respond.
- Examine the results. The IP addresses, hostnames, and locations of the DNS servers should all belong to your VPN provider. You might see names like “Google” or “Cloudflare” if your VPN uses them for privacy, which is generally safe.
- If you see the name of your actual Internet Service Provider (e.g., Comcast, Verizon, BT Group), you have a DNS leak. Your browsing history is visible to your ISP.
4. How to Check for a WebRTC Leak
WebRTC, which stands for Web Real-Time Communication, is a technology built into most modern browsers like Chrome, Firefox, and Edge. It enables real-time voice, video, and data communication directly between browsers without needing extra plugins. While useful for applications like video chat and file sharing, WebRTC can pose a serious security risk for VPN users.
A WebRTC leak can occur because the technology uses specific protocols to discover your real IP address to facilitate a direct connection, and these requests can sometimes happen outside the VPN’s encrypted tunnel. This means a website could run a simple piece of code in your browser and uncover your true IP address, even when your VPN appears to be working perfectly.
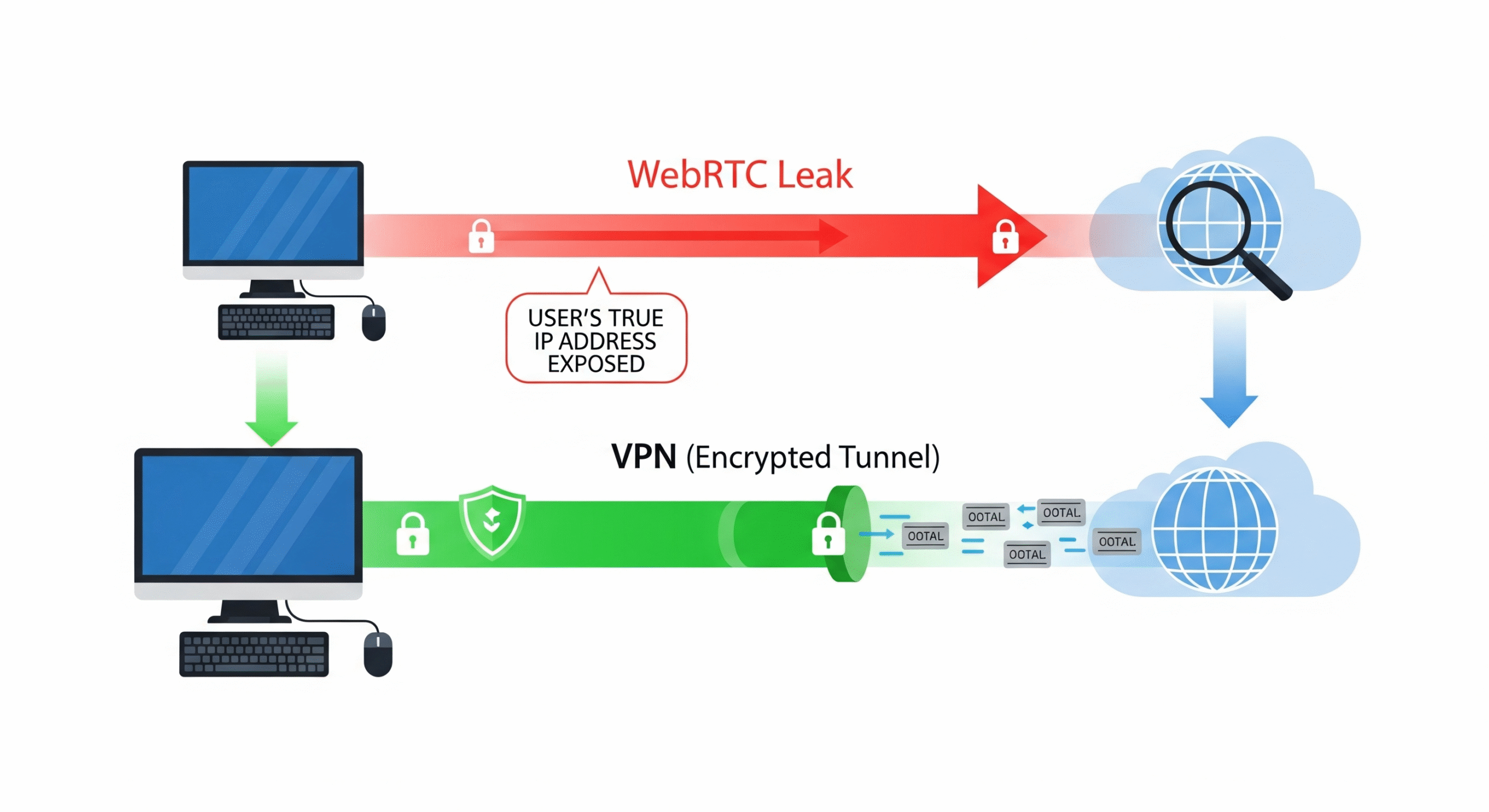
4.1. How to Verify a WebRTC Leak
You can easily check for this vulnerability. With your VPN active, visit a testing site like BrowserLeaks.com/webrtc.
- The page will automatically run a test and display the results under “WebRTC IP Address Detection.”
- Look at the “Public IP Address” field. This should show the IP address assigned by your VPN, not your real IP address from Step 1 of the basic test.
- If your real IP address is visible anywhere on the page, you have a WebRTC leak.
5. Solutions and Next Steps If You Find a Leak
Discovering a leak can be alarming, but don’t panic. In many cases, these issues can be fixed. Here’s what to do.
5.1. Enable Built-In Leak Protection
Most reputable VPN services include built-in protection against these leaks. Dive into your VPN application’s settings and look for options like:
- Kill Switch: This is a critical feature that automatically blocks all internet traffic if your VPN connection drops, preventing any data from leaking out.
- DNS Leak Protection: An explicit setting that ensures all DNS queries are forced through the VPN’s servers.
- IPv6 Leak Protection: Some VPNs may not handle IPv6 traffic, which can cause leaks on networks that use it. This setting usually disables IPv6 traffic to prevent exposure.
5.2. Address WebRTC Leaks
If you have a WebRTC leak, you can often fix it at the browser level:
- Browser Extensions: Install a reputable extension like uBlock Origin or WebRTC Leak Prevent, which can block WebRTC requests.
- Disable WebRTC in Firefox: Type
about:configinto the address bar, search formedia.peerconnection.enabled, and double-click it to set it tofalse.
5.3. Change Servers or Protocols
Sometimes, a leak can be specific to a certain server or connection protocol (e.g., OpenVPN, IKEv2, WireGuard). Try connecting to a different server location. If the leak persists, go into your VPN settings and switch to a different protocol and run the tests again.
5.4. Contact Your VPN Provider’s Support
If you’ve tried the steps above and still find leaks, it’s time to contact your VPN provider’s technical support. A trustworthy company should be able to help you diagnose and fix the problem. If they can’t, or if they are unresponsive, it’s a major red flag.
6. GenFarmer’s Optimal Solution for Ultimate Security
For serious MMO professionals, digital marketers, and businesses running large-scale operations, relying on a standard consumer VPN is not enough. You need an integrated, controllable, and robust infrastructure. This is where GenFarmer provides a comprehensive solution that goes beyond basic IP masking.
- Hardware-Level Control: Our Router Proxy devices are engineered to give you complete control over your network environment. Instead of relying on software that can fail or leak, you manage your IPs at the hardware level, creating a more secure and stable foundation for all your devices.
- Scalable and Centralized Management: The GenFarmer ecosystem, including our Box Phone Farm hardware, is designed for scalability. You can manage hundreds of devices from a single, secure interface, ensuring consistent security policies and operational efficiency without the risk of individual software failures.
- Secure Virtual Environments: Our Cloud Phone service provides pristine virtual devices, minimizing the risk of software conflicts and leaks inherent in physical or emulated devices. Each instance is isolated, providing another layer of security for your automated tasks.

By integrating hardware, cloud solutions, and automation software, GenFarmer helps you build a private, controlled, and leak-proof infrastructure tailored for high-demand professional use.
Conclusion: Trust, But Verify
A VPN is a powerful tool for digital privacy, but it is not infallible. Regularly performing these simple checks for IP, DNS, and WebRTC leaks is an essential habit for anyone serious about their online security. It ensures you are getting the protection you paid for and that your digital cloak remains intact.
Just as it’s crucial to ensure your VPN is secure, it’s vital to have reliable and secure tools for your digital marketing and MMO activities. A compromised IP can derail your entire operation. At GenFarmer, we provide a complete ecosystem built for automation and security. Our hardware solutions like the Box Phone Farm and the Router Proxy devices are engineered for stability and performance. Our Cloud Phone service offers secure, virtual devices for your tasks. Elevate your strategy with our specialized automation suites like GenFarmer Facebook Boost and GenFarmer TikTok Boost to manage and grow your social media accounts securely and efficiently. Explore the GenFarmer ecosystem today and build your operations on a foundation of trust and performance.











