IP Rotation and Fingerprinting are at the core of how platforms identify and track users in the complex world of digital marketing, social media management, and online market operations (MMO). Your online identity is more than just a username and password—companies like Google, Facebook, and TikTok use advanced tracking methods that go beyond your IP address to profile your behavior. For those managing multiple accounts, understanding these mechanisms isn’t just an advantage—it’s essential for survival.
1. The Basics of IP Management: Static vs. Rotating
At the most fundamental level, your IP address is your digital passport, a unique identifier for your device on the internet. However, not all passports are created equal. The first step in learning how to manage multiple IPs is understanding the core difference between static and rotating addresses.
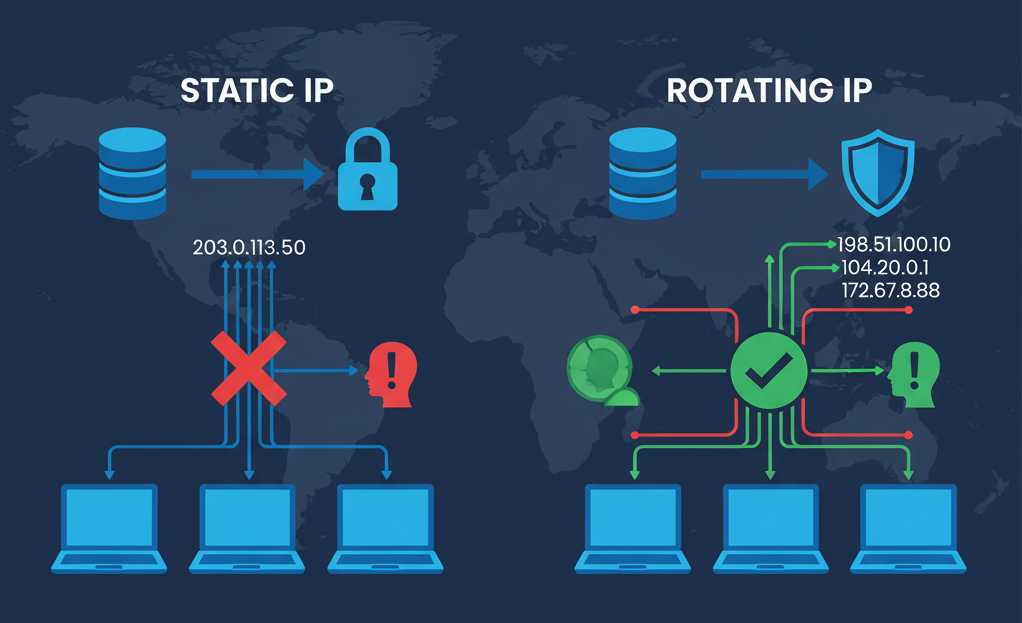
1.1. Static IPs: The Consistent Presence
A static IP address is a fixed, unchanging number assigned to your device. Think of it as a permanent home address. For everyday internet use, this is perfectly fine. However, when managing multiple accounts, a single static IP is a red flag. If ten different Facebook accounts all log in consistently from the same IP, the platform will quickly connect them and may issue restrictions or bans.
- Pros: Stable, reliable, sometimes required for whitelisting access to secure systems.
- Cons: Easily traceable, creates a clear link between all associated accounts, high risk for multi-account management.
1.2. Rotating IPs: The Art of Digital Camouflage
A rotating IP, or dynamic IP, changes periodically. The change can happen every few minutes, every few hours, or with every new connection request. This is the cornerstone of professional multi-account management. By rotating IPs, you make it appear as if each account is being operated from a different location and device, drastically reducing the risk of being detected.
- Pros: Enhances anonymity, breaks the link between accounts, essential for web scraping and large-scale account management.
- Cons: Can be unstable if sourced from low-quality providers, requires careful management to appear natural.
2. Advanced IP Rotation Techniques
Simply using rotating IPs isn’t enough. The way you rotate them matters. The two primary methods are per-request rotation and “sticky” sessions, and choosing the right one depends entirely on your task.
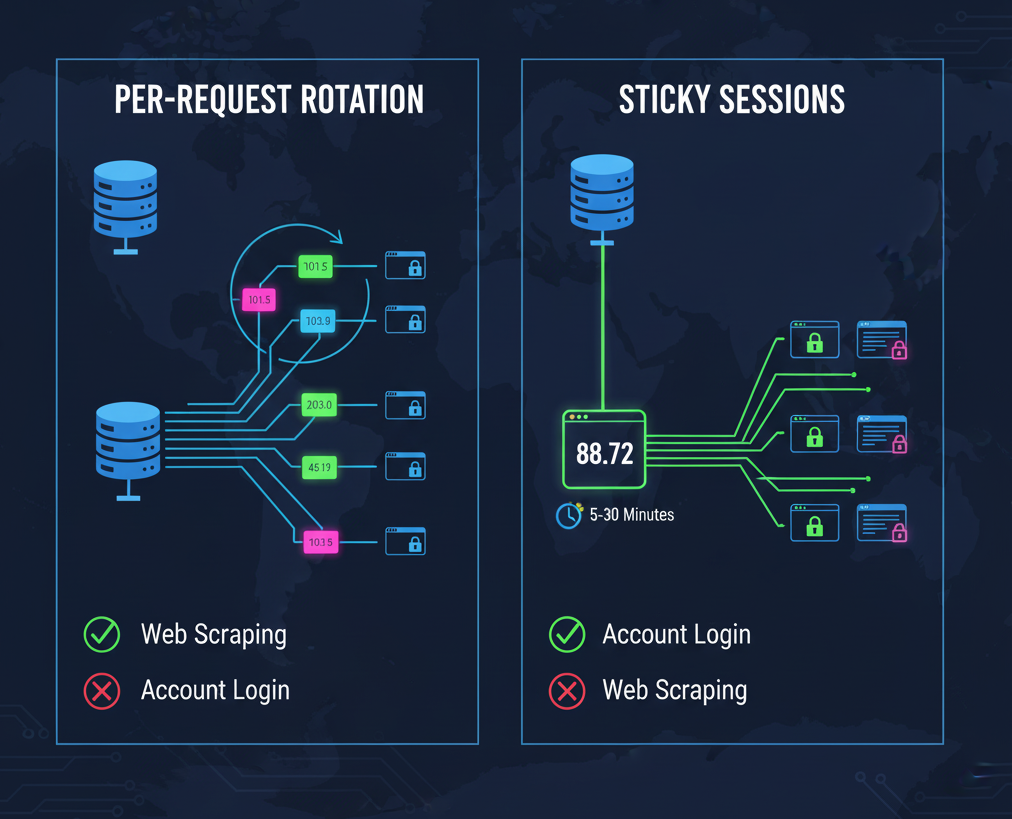
2.1. Rotation Per Request
In this model, your IP address changes with every single request sent to a server. This is highly effective for tasks like web scraping, where you need to gather large amounts of data from a website without being rate-limited or blocked. Each request appears to come from a new user, allowing you to fly under the radar.
2.2. Sticky Sessions
A sticky session maintains the same IP address for a set period—say, 5, 10, or 30 minutes. This is absolutely critical for any task that involves logging into an account. Imagine logging into your Instagram account from an IP in California. If you then “like” a post two seconds later from an IP in New York, the platform will instantly flag your account for suspicious activity. A sticky session ensures that all actions within a single session appear to come from the same legitimate user, maintaining a consistent and believable identity.
3. Beyond the IP: An Introduction to Device Fingerprinting
Here’s where many automation strategies fail. They focus so much on how to manage multiple IPs that they forget the other half of the equation: the device fingerprint. A device fingerprint is a unique profile created by collecting a host of technical details about your device and browser. This includes:
- User-Agent String: Information about your browser and operating system.
- Screen Resolution and Color Depth: The size and capabilities of your display.
- Installed Fonts: The list of fonts on your system.
- Browser Plugins and Extensions: The add-ons you have installed.
- Timezone and Language Settings: Your geographical and language preferences.
- Canvas and WebGL Fingerprinting: Advanced techniques that render hidden graphics to create a highly unique hardware signature.
Combined, these data points create a “fingerprint” that is often more unique than your IP address. Platforms use this to identify you even if you change your IP. If you’re running multiple accounts from the same computer, they might all share the same device fingerprint, creating an easily detectable pattern.
4. The Deadly Combination: Mismatched IPs and Fingerprints
The real danger lies in the mismatch between your IP and your device fingerprint. This is the amateur mistake that gets accounts banned. Consider these two fatal scenarios:
- One Fingerprint, Many IPs: You use an advanced IP rotation service that gives you a new IP every minute. However, you’re running all your accounts from a single browser profile. The platform sees one unique device fingerprint (Your PC) associated with hundreds of different IPs from all over the world in a short time. This is an impossible scenario for a real user and a massive red flag.
- One IP, Many Fingerprints: You use software that creates unique device fingerprints for each account but run them all through your single home IP address. The platform sees dozens of completely different “devices” all operating from the same network. This is equally suspicious and signals the use of automation tools.
True stealth requires consistency. Each online identity must have its own unique, persistent device fingerprint paired with a clean, corresponding IP address. The IP might change (rotate), but it must do so in a believable way for that specific fingerprint profile.
5. The Holistic Solution: The GenFarmer Ecosystem Approach
Managing this complex interplay between IPs and fingerprints manually is nearly impossible at scale. It requires a comprehensive, integrated solution where the network layer and the device layer work in perfect harmony. This is precisely what the GenFarmer ecosystem is designed for.
5.1. Step 1: Perfecting the Network with GenRouter
Your foundation is the network. The GenRouter Proxy is more than just a router; it’s a specialized hardware solution engineered to handle sophisticated IP routing and rotation. It ensures that each of your devices or virtual profiles is assigned a clean, stable IP, with advanced options for managing sticky sessions and geo-location. It solves the IP side of the puzzle flawlessly.

5.2. Step 2: Mastering the Device with GenFarmer Trust
With the network layer handled, you need to manage the device layer. Our automation solutions, such as GenFarmer Trust for Facebook or GenFarmer TikTok Trust, are built to manage device fingerprints intelligently. Each account you manage is given its own unique, persistent environment. The software doesn’t just randomize fingerprints; it creates and maintains believable profiles that mimic real user devices. This ensures that every action performed for an account is consistent with its established digital identity.
When you combine GenRouter with GenFarmer’s software, you create a seamless system. The router assigns a clean IP to a specific phone or profile, and the software ensures that the device fingerprint on that profile is unique and consistent. The result is a collection of truly separate and believable online identities, invisible to even the most advanced detection systems.
Conclusion: Building Your Digital Fortress
In 2025 and beyond, successfully managing multiple online identities requires a two-layer defense strategy. Focusing only on how to manage multiple IPs is like locking the front door but leaving all the windows open. You must control both the network (IPs) and the device (fingerprints) to create a truly secure and resilient operation.
By treating each account as a complete identity—with its own IP history and its own device fingerprint—you move from amateur automation to professional, undetectable asset management. This is the methodology that separates temporary gains from long-term, scalable success.
Are you ready to build your digital fortress? Explore our ecosystem of solutions at GenFarmer.com. From our powerful Box Phone Farm hardware and Proxy Routers to our intelligent Cloud Phones and automation software, we provide the end-to-end tools you need to thrive in the digital landscape.











