In today’s digital world, knowing how to hide my IP address has become essential. Your IP address is like your physical address on the internet, revealing your location and allowing third parties to track your activity. Hiding it is a crucial step to protect your privacy, enhance your online security, and access content that may be restricted in your region. This guide will clearly and directly show you three effective methods to do just that.
Method 1: Use a VPN (The Safest and Most Recommended Option)
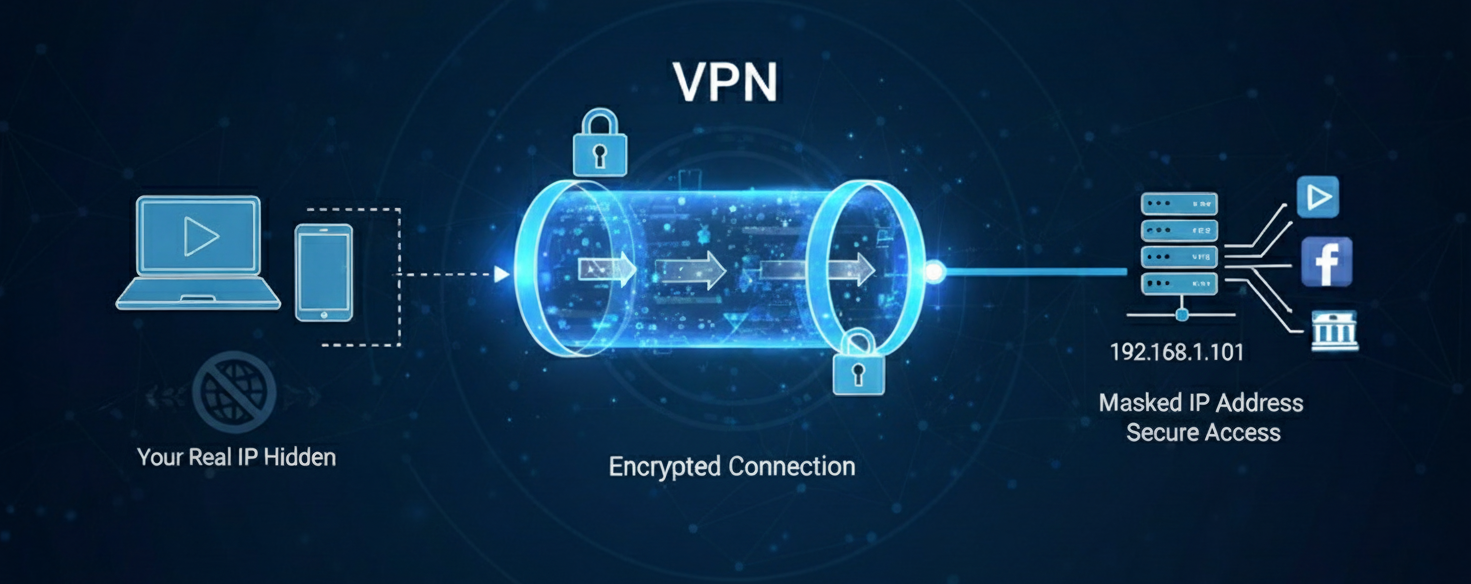
Using a Virtual Private Network (VPN) is the most comprehensive and secure method to hide your IP. A VPN not only masks your real IP address but also encrypts your entire internet connection. This means no one, not your Internet Service Provider (ISP) nor potential snoops, can see what you do online.
Why is it the best choice?
The main advantage of a VPN is its comprehensive protection. By routing your traffic through a secure server, it assigns you a new IP from that server’s location. But most importantly, it provides encryption. This secure tunnel protects all your data, from browsing to app usage, making it ideal for using public Wi-Fi networks and handling sensitive information. It’s the perfect combination of privacy and security.
Step-by-Step Guide to Using a VPN:
- Choose and subscribe to a reliable VPN provider: Research and select a VPN service with a strong no-logs policy and good speeds.
- Download and install the application: Most providers offer easy-to-use apps for all your devices, including PC, Mac, Android, and iOS.
- Connect to a server: Open the app, log in with your credentials, and select a server from the list. You can choose a specific country to access its content or use the “quick connect” option for the best speed. Once connected, your IP will be hidden, and your connection encrypted.
Method 2: Use a Proxy Server (A Fast but Less Secure Option)
A proxy server acts as an intermediary between your device and the internet. When you use one, your traffic first goes to the proxy, which replaces your IP address with its own before sending it to the destination website. It’s a quick way to mask your IP, but with a key difference from a VPN: most proxies do not encrypt your traffic.

When should you consider it?
A proxy is useful for quick tasks that don’t involve personal or sensitive information. For example, if you just want to access a geo-blocked website or avoid simple IP-based tracking. However, due to the lack of encryption, it is not recommended for logging into bank accounts, emails, or any activity that requires security.
Step-by-Step Guide to Using a Proxy:
- Web Proxy: This is the simplest way. Just visit a web proxy site, paste the URL of the site you want to visit into its search bar, and the proxy will load the page for you, hiding your IP. It’s fast and requires no installation.
- Browser Configuration (Chrome): For more integrated use, you can configure a proxy directly in your browser.
- Open Chrome and go to Settings (the three dots in the top right corner).
- In the left-hand menu, click on System.
- Select “Open your computer’s proxy settings”.
- In the new window, under the “Manual proxy setup” section, turn on the “Use a proxy server” option.
- Enter the IP address and port of the proxy server you want to use (you can find lists of free proxies online, though paid ones are more reliable).
- Save the changes. Now all your browser traffic will go through the proxy.
At GenFarmer, we understand the need for robust and flexible IP management. That’s why our proxy routers are designed to offer centralized and efficient control, ideal for automation and large-scale digital marketing tasks.

Method 3: Use the Tor Network (Maximum Anonymity with Sacrifices)
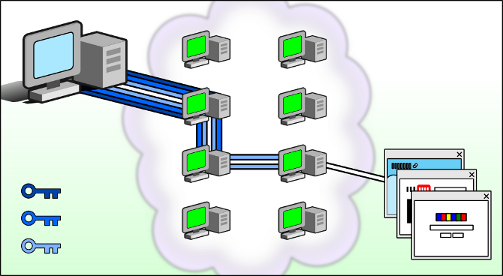
Tor (The Onion Router) is a volunteer-operated network from around the world that offers a high degree of anonymity. Its name comes from the “onion layers” of encryption it uses to protect your identity.
How does it work?
Simply put, Tor routes your internet traffic through a series of at least three random servers (called relays or nodes) before it reaches its final destination. Each relay only knows the identity of the previous and next relay, so no single point in the path knows both the origin and destination of the data. This makes tracing the activity back to the original user extremely difficult.
The Downsides of Tor:
- Slowness: Due to the multiple layers of encryption and relaying, browsing speed on the Tor network is significantly slower than with a VPN or proxy. It is not ideal for streaming or large downloads.
- Limited Protection: Tor only protects traffic that passes through the Tor Browser. It does not protect other applications or activities on your device.
- Association with Illicit Activities: Although Tor has many legitimate uses (journalism, activism in oppressive regimes), it is also the gateway to the “dark web.” Its use can raise suspicion from your ISP or authorities, even if your intentions are harmless.
Other Methods (Brief Mentions)
There are other ways to change your IP, although they are less effective for privacy:
- Connecting to a Public Wi-Fi Network: When you use public Wi-Fi, you temporarily use that network’s IP address. However, these networks are very insecure and expose you to other risks. It’s also not a practical long-term solution.
- Restarting Your Router: If your ISP assigns you a dynamic IP address (most do), restarting your router may cause them to assign you a new one. This can work to bypass a simple block, but it offers no anonymity or security, and your new IP is still linked to you.
Conclusion: Which is the Best Method for You?
Knowing how to hide my IP address is essential, and the choice of method depends on your needs. For robust security, complete privacy, and ease of use, a VPN is the superior option. For quick tasks where security isn’t a concern, a proxy may suffice. Tor offers maximum anonymity but at the cost of speed and usability.
For those in the MMO, digital marketing, and business worlds who require advanced management of multiple profiles and connections, the solution goes beyond a simple IP change. At GenFarmer, we offer a complete ecosystem for automation, from our Box Phone Farms to Cloud Phone solutions and specialized hardware like our Proxy Router. Our tools are designed to give you the control, security, and efficiency you need to scale your operations safely.
Contact us now to get the best solutions!











