You’ve felt the frustration: after investing heavily in a phone farm for your MMO or social media business, a sudden wave of mass bans wipes out your entire operation. This isn’t bad luck; it’s a technology gap. The platforms you use, from TikTok to Facebook, are in a constant arms race against automation, deploying sophisticated, multi-layered risk detection. The core of the problem is this: your setup is based on simulation, and their systems are built to find and destroy anything that isn’t authentic.
Welcome to the new battlefield of automation, where the only way to win is to be indistinguishable from a real user. This guide will break down exactly how you are being detected and introduce the only real solution: the true anti-detect phone farm built on hardware-level isolation.
The Detection Matrix: Why Your Current Phone Farm Fails
To build an anti-detect phone farm, you must first understand what you’re fighting. Platform risk control isn’t one single check; it’s a “Detection Matrix” built on three pillars. Your farm is likely failing one, if not all, of them.
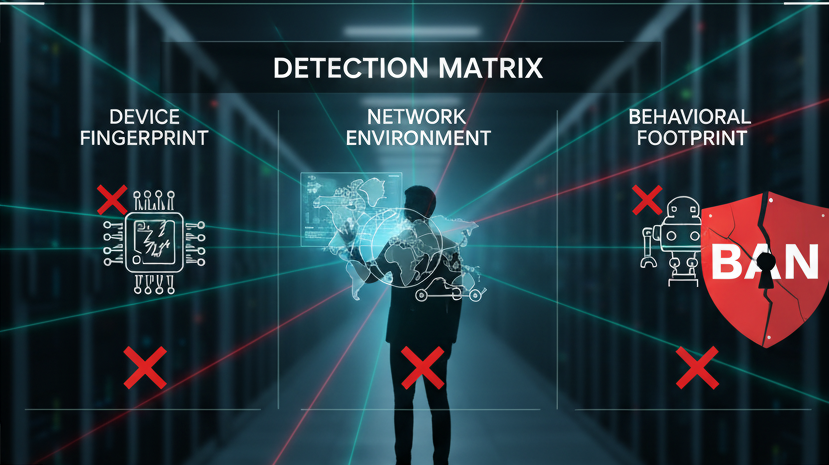
Pillar 1: The Device Fingerprint (The “Digital DNA”)
A device fingerprint is a unique identifier collected from your phone. It’s far more than just an IP address. It includes:
- Hardware IDs: IMEI, MAC Address, CPU Serial Number, Motherboard ID.
- System Properties:
Build.FINGERPRINT,ro.product.model,ro.product.brand. This tells the platform if you’re a “Samsung SM-G998U” or a “Generic Android Emulator.” - Sensor Data: The presence (or absence) of a gyroscope, accelerometer, battery sensor, and light sensor.
How They Catch You: Most “cloud phones” and virtual machine (VM) solutions are disasters for fingerprinting. They are often Docker containers or basic emulators that share the same underlying system, or kernel. This means hundreds of your “devices” might report identical hardware data (e.g., “QEMU Virtual CPU” or test-keys in the build signature). To a platform like TikTok, this isn’t just a red flag; it’s a confession. You are screaming that you are not a real user.
Pillar 2: The Network Environment (The “Digital Address”)
This is where many operators think they’re safe because they use proxies. But the network environment is deeper than that.
- IP Reputation: Is your IP from a residential address or a known datacenter? Datacenter IPs (used by most cheap VPNs and proxies) are instantly suspicious.
- Environment Consistency: Does your IP’s geographic location match your phone’s system language, timezone, and SIM card information (MCC/MNC)? A device in Los Angeles (IP) with a Vietnamese SIM card and a New York timezone is an obvious fraud.
- Network Fingerprint: Platforms can even analyze your TCP/IP stack and DNS settings, which often reveal the use of a proxy or VM.
How They Catch You: You run 100 accounts through a single datacenter proxy, or your proxy’s location doesn’t match your device’s “story.” This lack of consistency flags your entire operation for review and suspension.
Pillar 3: The Behavioral Footprint (The “Human Element”)
This is the most advanced pillar and the one that defeats almost all basic automation scripts. Platforms don’t just watch “what” you do; they watch “how” you do it.
- Interaction Patterns: Do you tap the exact same (X,Y) coordinate every time you hit “like”? A human can’t. Your finger pressure, swipe speed, and even the slight curve of your swipe are all unique behavioral biometrics .
- Sensor Activity: When a real person holds a phone, the gyroscope and accelerometer report constant, tiny micro-movements. A phone running a script on a rack is perfectly still. This “dead sensor” data is a clear sign of an unmanned device.
- Usage Habits: Does your “phone” only have TikTok and Instagram installed? A real user has email, a web browser, a weather app, and junk games. Is your device active 24/7 without sleep? Real humans don’t do that.
How They Catch You: Your adb shell input tap scripts are robotic and precise. Your devices are unnaturally still, perfectly clean, and always active. You are failing the “digital Turing test.”
The Solution: What Is a True Anti-Detect Phone Farm?
A true anti-detect phone farm is not a single piece of software. It is an ecosystem designed to defeat all three pillars of the Detection Matrix by prioritizing one thing: authenticity.
This solution is built on a concept called Hardware-Level Isolation. Instead of using fake, shared virtual machines, this method uses “real mobile hardware” or deeply virtualized instances that are assigned dedicated, non-shared physical resources.
Here is how this approach creates a truly undetectable device:
- It Fixes the Fingerprint: Each device in the farm is a separate motherboard or hardware-isolated instance. This means each one provides unique, authentic hardware IDs, real CPU information, legitimate build properties, and verifiable battery and sensor data. It looks real because it “is” real.
- It Fixes the Network: A professional anti-detect phone farm setup allows you to assign a unique, clean residential or 4G/5G mobile proxy to “each” physical device. You can then match the device’s system language and timezone to the proxy’s location, creating a perfectly consistent digital identity.
- It Fixes the Behavior: This is the final piece. Instead of robotic scripts, advanced anti-detect systems use AI-powered automation to simulate “human” behavior . This includes adding random delays, creating non-linear swipes, simulating sensor data (like tilting the phone), and even background “junk” activity to make the device look used and natural.
Box Phone Farm vs. Cloud Phone: Choosing Your Anti-Detect Solution
You have two primary paths to achieve hardware-level isolation. Both are valid, and GenFarmer provides solutions for both.
1. Box Phone Farm (The Hardware-First Approach)
A box phone farm (or “phone box”) is a physical chassis that holds and manages multiple real mobile phone motherboards. This is the ultimate “anti-detect” solution because it uses 100% real hardware.
- Pros:
- Total Authenticity: You are using real Samsung, Google, or other motherboards. Detection is nearly impossible at the hardware level.
- Full Control: You own the hardware. You control the power, cooling, and network connections.
- One-Time Cost: It’s a one-time capital investment in hardware rather than a recurring subscription.
- Cons:
- Upfront Investment: Requires purchasing the hardware.
- Physical Management: You need physical space and must manage power, cooling, and networking.
2. Anti-Detect Cloud Phone (The “Real Machine” Cloud)
Warning: This is “not” the standard, cheap “cloud phone” service that gets you banned. Those are just VMs. A true anti-detect cloud phone service, like the one GenFarmer offers, provides you with a dedicated, hardware-isolated “real machine” instance in the cloud.
- Pros:
- Instant Scalability: Go from 10 devices to 1,000 devices in minutes without buying hardware.
- Zero Maintenance: We handle the hardware, power, and cooling. You just focus on your business.
- Pay-As-You-Go: A flexible operational expense instead of a large capital expense.
- Cons:
- Recurring Cost: You are renting the hardware.
- Requires Trust: You must choose a provider (like GenFarmer) that “guarantees” true hardware-level isolation and doesn’t just resell detectable VMs.
The GenFarmer Ecosystem: Your Complete Anti-Detect Toolkit
Building a successful, ban-proof operation requires more than just one tool. It requires a complete ecosystem that addresses all three pillars of detection. This is what we’ve built at GenFarmer.
- For the Hardware Foundation (Pillar 1):
- Our Box Phone Farm hardware gives you the physical, undetectable base you own and control.
- Our Cloud Phone service provides scalable, pay-as-you-go “real machine” instances, not the cheap VMs that get you banned.

GenFarmer Box Phone Farm 
Cloud Phone – GenFarmer - For Network Control (Pillar 2):
- Our Router Proxy hardware and MiniPCs allow you to build and manage sophisticated, clean network environments, assigning unique residential IPs to every device.

Genrouter H3000 - For Intelligent Automation (Pillar 3):
- This is our specialty. Our automation software, like GenFarmer Trust (for Facebook) and GenFarmer TikTok Boost, is not a simple script. It’s an AI-powered automation platform that simulates “real human behavior”. It performs actions with human-like randomness, interacts with sensors, and builds account history naturally. It’s the “human soul” for your hardware body.
Conclusion: Stop Building on Sand
Stop fighting multi-billion dollar platforms with broken, outdated tools. The battleground has moved from the app layer to the hardware layer. The only way to build a sustainable, scalable, and profitable operation is to be undetectable.
The solution is authenticity. You need an anti-detect phone farm built on a foundation of real (or perfectly isolated) hardware, clean network environments, and intelligent, human-like automation. Trying to cut corners with cheap VMs or basic scripts is no longer a risk; it’s a guarantee of failure.
Don’t let another mass ban wipe out your business. Explore the GenFarmer ecosystem today. Whether you choose the control of our Box Phone Farm hardware or the scalability of our Anti-Detect Cloud Phones, we provide the foundation of trust and technology you need to succeed.











